Security breaches are rising, yet many businesses overlook rigorous checks on their own controls. For organizations aiming to win client trust and prove they take data protection seriously, a SOC Type II Report is more than a formality. These assessments demand sustained performance and furnish stakeholders with clarity that routine audits cannot match. Discover how understanding SOC Type II can give your organization a real edge, safeguard valuable data, and support stronger business relationships.
Table of Contents
- Defining SOC Type II Report And Its Purpose
- Key Components Of SOC Type II Audit
- SOC 1 Vs. SOC 2 Vs. SOC Type II Explained
- Compliance, Preparation, And Common Challenges
- Risks, Costs, And Value For Organizations
Key Takeaways
Defining SOC Type II Report And Its Purpose
A SOC Type II Report is a comprehensive security assessment that evaluates an organization’s controls and processes against predefined trust service criteria. According to Grant Thornton, these reports provide users with a detailed description of an organization’s system, including service commitments, system requirements, and key infrastructure components used in service delivery.
Unlike other security assessments, SOC Type II reports go beyond surface-level evaluations. They involve an in-depth examination of a company’s operational controls over a minimum six-month period, offering stakeholders a thorough understanding of an organization’s security practices. As Department of Labor documentation indicates, these examinations are performed under the broader ISAE 3000 standard, which ensures a rigorous and standardized approach to security assessment.
The primary purpose of a SOC Type II Report centers on building trust and demonstrating compliance. Key objectives include:
- Providing independent verification of an organization’s security controls
- Offering transparent insights into risk management processes
- Helping potential clients evaluate an organization’s commitment to data protection
- Serving as a critical tool for vendor risk management
By generating a comprehensive SOC Type II Report, organizations can effectively communicate their security posture, instill confidence among stakeholders, and validate their commitment to maintaining robust, reliable operational controls.
Key Components Of SOC Type II Audit
A SOC Type II Audit involves a comprehensive evaluation of an organization’s security controls and operational processes. Grant Thornton emphasizes that the report provides critical assurances about whether the controls have been designed and operate effectively to achieve the entity’s service commitments and system requirements.
The key components of a SOC Type II Audit are structured around several essential elements that provide a holistic view of an organization’s security posture. As Department of Labor documentation highlights, a Type 2 SOC report includes an in-depth opinion on both the suitability of design and the operating effectiveness of controls.
Critical components of the SOC Type II Audit include:
- Trust Service Criteria: Evaluation against predefined security, availability, processing integrity, confidentiality, and privacy standards
- Control Effectiveness Assessment: Detailed examination of operational controls over a minimum six-month period
- System Description: Comprehensive overview of the organization’s infrastructure, processes, and service commitments
- Auditor’s Opinion: Independent verification of control design and operational effectiveness
- Detailed Testing Results: Specific evidence and documentation of control implementation and performance
The audit process is designed to provide stakeholders with a transparent and rigorous assessment of an organization’s security practices, offering deep insights into its risk management and control environment.
 Understanding the SOC Report: What It Is and Why It Matters can provide additional context for organizations seeking to comprehend the nuanced landscape of security assessments.
Understanding the SOC Report: What It Is and Why It Matters can provide additional context for organizations seeking to comprehend the nuanced landscape of security assessments.
SOC 1 vs. SOC 2 vs. SOC Type II Explained
Navigating the world of security compliance reports can be complex, with SOC 1, SOC 2, and SOC Type II often causing confusion among professionals. Department of Labor documentation provides crucial insights into the distinctions between these different types of reports, highlighting that each serves a unique purpose in assessing organizational controls.
SOC 2 reports, in particular, have a specific focus that sets them apart from other compliance assessments. According to Grant Thornton, these reports evaluate controls based on the American Institute of Certified Public Accountants (AICPA’s) Trust Services Criteria, which encompass five critical domains:
- Security: Protecting against unauthorized access
- Availability: Ensuring systems are accessible as committed
- Processing Integrity: Maintaining accurate and timely data processing
- Confidentiality: Protecting sensitive information
- Privacy: Managing personal information according to commitments
To help clarify the key differences, organizations can explore Understanding SOC II Type 1: What You Need to Know for more nuanced insights.
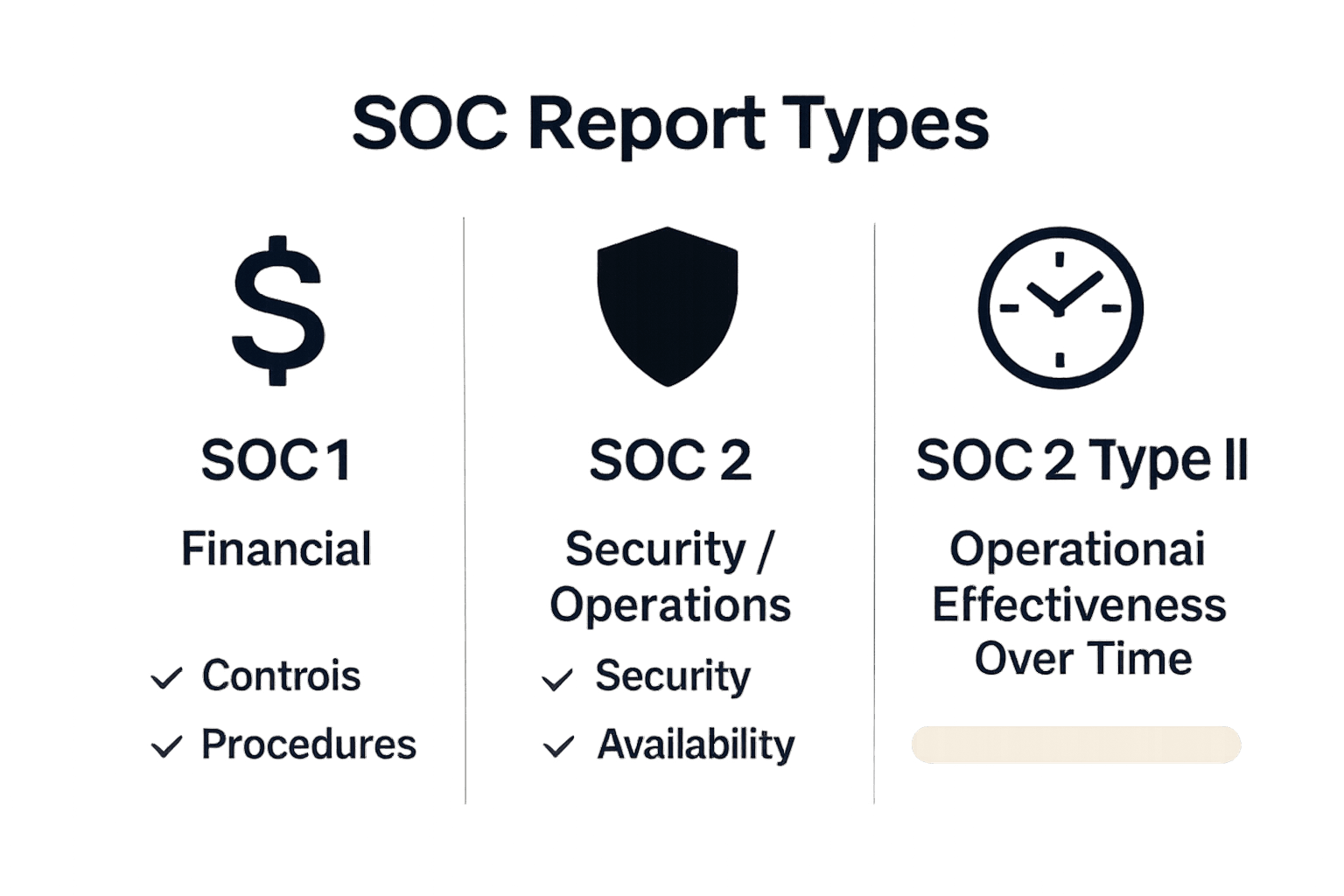 While SOC 1 primarily focuses on financial reporting controls, SOC 2 and SOC Type II reports provide a broader examination of an organization’s operational controls, with SOC Type II specifically involving a detailed assessment of control effectiveness over a minimum six-month period. This comprehensive approach offers stakeholders a deep, time-tested view of an organization’s security and operational practices.
While SOC 1 primarily focuses on financial reporting controls, SOC 2 and SOC Type II reports provide a broader examination of an organization’s operational controls, with SOC Type II specifically involving a detailed assessment of control effectiveness over a minimum six-month period. This comprehensive approach offers stakeholders a deep, time-tested view of an organization’s security and operational practices.
Compliance, Preparation, And Common Challenges
SOC Type II compliance represents a critical milestone for organizations seeking to demonstrate robust security practices. Grant Thornton emphasizes that a SOC 2 report has become an essential tool for doing business, especially when targeting clients across multiple jurisdictions.
Preparing for a SOC Type II audit involves a comprehensive and strategic approach that goes beyond simple checkbox compliance. Department of Labor documentation highlights the importance of demonstrating both the suitability of design and the operating effectiveness of controls.
Common challenges organizations face during SOC Type II preparation include:
- Documentation Gaps: Inadequate or inconsistent documentation of security controls
- Cultural Resistance: Difficulty in implementing consistent security practices across the organization
- Resource Constraints: Limited time and personnel to prepare comprehensive audit documentation
- Complex Control Environments: Managing controls across multiple systems and platforms
- Continuous Monitoring: Maintaining consistent control effectiveness over the audit period
To navigate these challenges effectively, organizations can leverage 7 Steps to Create a Complete SOC 2 Compliance Checklist to streamline their preparation process. Successful SOC Type II compliance requires a proactive approach, combining thorough documentation, consistent control implementation, and a commitment to ongoing security improvement.
Risks, Costs, And Value For Organizations
SOC Type II reports represent a strategic investment that goes far beyond mere compliance. Grant Thornton underscores that these reports have become an essential tool for businesses targeting clients across multiple jurisdictions, highlighting their critical role in modern organizational risk management.
Department of Labor documentation reveals the multifaceted nature of SOC Type II assessments, which provide a comprehensive opinion on both control design and operational effectiveness. This depth of analysis translates into tangible benefits and potential risks for organizations.
Key organizational considerations include:
- Financial Investment: Typical SOC Type II audit costs range from $20,000 to $100,000 depending on organizational complexity
- Competitive Advantage: Demonstrating robust security controls can differentiate organizations in competitive markets
- Risk Mitigation: Identifying and addressing potential security vulnerabilities before they become critical issues
- Client Trust: Providing transparent evidence of security and operational excellence
- Potential Compliance Penalties: Avoiding potential legal and financial consequences of inadequate security controls
What is Vendor Risk Management? offers additional context for understanding how SOC Type II reports play a crucial role in comprehensive risk management strategies. While the initial investment may seem substantial, the long-term value of a SOC Type II report far outweighs the costs by building organizational credibility, reducing potential security risks, and demonstrating a commitment to maintaining the highest standards of operational integrity.
Simplify SOC Type II Compliance With Skypher’s AI-Driven Automation
Achieving and maintaining SOC Type II compliance demands rigorous control documentation and ongoing operational effectiveness organization-wide. The article highlights key challenges like documentation gaps and continuous monitoring that can delay or derail your audit preparation. Skypher’s AI Questionnaire Automation Tool tackles these pain points by drastically reducing the time spent on security questionnaires while boosting accuracy and collaboration across teams. Our platform integrates seamlessly with over 40 third-party risk management systems to streamline your compliance workflows and help sustain a consistent, transparent security posture.

Don’t let complex SOC Type II audits slow your business growth. Experience how Skypher’s customizable Trust Center and real-time integrations can empower your team to complete assessments faster and with more confidence. Start transforming your compliance process now by visiting Skypher. Learn more about how our AI Questionnaire Automation Tool and API Integrations with TPRM Platforms deliver the efficiency and control your organization needs.
Frequently Asked Questions
What is a SOC Type II Report?
A SOC Type II Report is a comprehensive security assessment that evaluates an organization’s controls and processes against predefined trust service criteria over a minimum six-month period. It provides independent verification of an organization’s commitment to data protection and offers transparent insights into risk management processes.
What are the key components of a SOC Type II Audit?
The key components include Trust Service Criteria evaluation, control effectiveness assessment, system description overview, auditor’s opinion, and detailed testing results. These elements provide a holistic view of an organization’s security posture and operational controls.
How does SOC Type II differ from SOC 1 and SOC 2 reports?
SOC 1 focuses on financial reporting controls, while SOC 2 and SOC Type II reports evaluate operational controls based on the principles of security, availability, processing integrity, confidentiality, and privacy. SOC Type II specifically assesses control effectiveness over a specified period.
What are common challenges organizations face when preparing for a SOC Type II audit?
Common challenges include documentation gaps, cultural resistance to consistent security practices, resource constraints, managing complex control environments, and maintaining continuous monitoring of control effectiveness throughout the audit period.




.png)
