Most American technology companies underestimate the true scope of SOC 2 compliance costs. With each additional trust service criterion, overall expenses can jump by 20 to 30 percent, making budgeting more complex than many firms expect. As data security demands rise for cloud service providers and SaaS businesses, understanding what drives compliance spending takes on real urgency. This guide reveals the key elements that shape SOC 2 budgets, helping technology leaders anticipate both obvious and hidden financial impacts.
Table of Contents
- SOC 2 Compliance: Definition and Purpose
- Core Elements Impacting SOC 2 Costs
- Direct and Indirect Expenses Explained
- Hidden Costs and Budgeting Pitfalls
- Strategies to Minimize SOC 2 Expenditure
Key Takeaways
SOC 2 Compliance: Definition and Purpose
SOC 2 compliance represents a critical cybersecurity framework that validates an organization’s commitment to protecting sensitive customer data. Developed by the American Institute of Certified Public Accountants (AICPA), this standard provides a comprehensive approach to evaluating an organization’s security protocols, particularly for technology and cloud service providers.
At its core, SOC 2 focuses on five key trust service criteria that organizations must demonstrate: security, availability, processing integrity, confidentiality, and privacy. When a company successfully achieves SOC 2 compliance, it signals to customers and stakeholders that robust internal controls are in place to safeguard critical information assets. These criteria go beyond basic technical controls, examining holistic operational processes that protect data throughout its lifecycle.
Here is a summary of the five SOC 2 trust service criteria and their business significance:
The framework is particularly crucial for technology firms, software-as-a-service (SaaS) providers, and cloud computing companies that handle sensitive client information. Unlike generic security standards, SOC 2 offers a flexible, customizable approach that allows organizations to design controls specific to their unique business environments and risk profiles. This adaptability makes it an essential benchmark for demonstrating technological and operational reliability in an increasingly complex digital landscape.
Pro Tip - Strategic Preparation: Start your SOC 2 compliance journey by conducting a comprehensive internal audit at least 6-9 months before your actual compliance assessment, identifying potential gaps and developing targeted remediation strategies.
Core Elements Impacting SOC 2 Costs
Understanding the core elements that influence SOC 2 compliance costs is crucial for technology firms planning their cybersecurity strategy. Organizations must recognize that SOC 2 compliance is not a one-size-fits-all expense, but a nuanced investment that varies significantly based on multiple critical factors.
The primary drivers of SOC 2 compliance expenses include the type of audit selected, organizational complexity, and the specific trust service criteria being evaluated. Comprehensive SOC 2 cost analyses reveal that each additional trust service criterion can increase overall compliance costs by 20-30%. Tech firms must carefully consider which criteria are most relevant to their operational model, as selecting more criteria directly correlates with higher audit complexity and associated expenses.

Key cost-determining factors encompass several technical and operational dimensions. These include the current maturity of existing security controls, the scale and complexity of organizational systems, and the depth of documentation required for demonstrating compliance. Companies with more sophisticated technological infrastructures or those operating in highly regulated industries will inevitably face more extensive audit requirements. Larger organizations with complex network architectures and multiple service lines will encounter more comprehensive assessment processes, which translate into higher compliance investment.
Pro Tip - Strategic Cost Management: Conduct a thorough internal readiness assessment at least 6 months before your planned SOC 2 audit to identify potential control gaps and implement cost-effective improvements, potentially reducing overall compliance expenses.
Direct and Indirect Expenses Explained
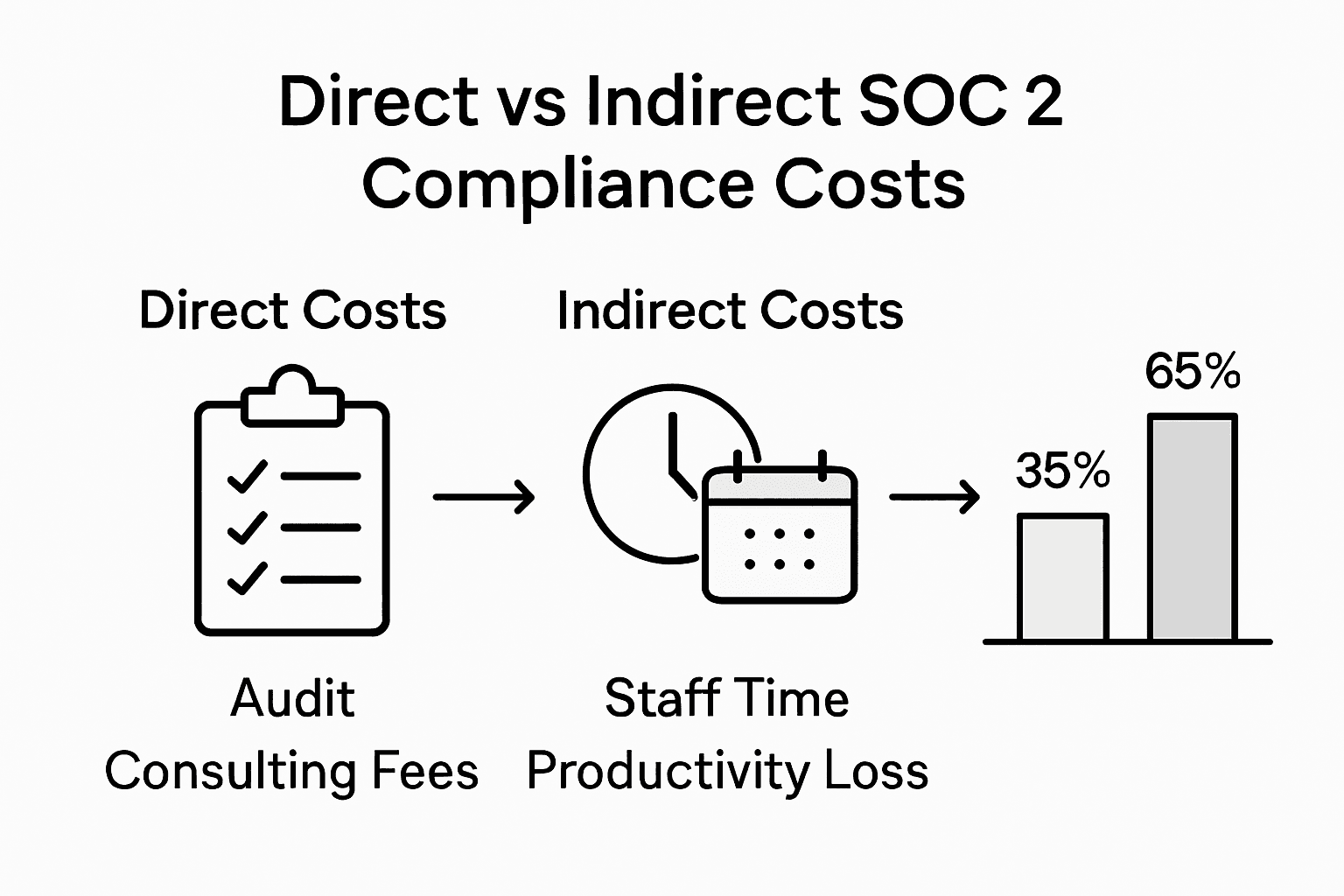
SOC 2 compliance involves a complex financial landscape where expenses extend far beyond simple audit fees. Technology firms must understand both direct and indirect costs to develop a comprehensive budgeting strategy that accounts for the full scope of compliance investments.
Direct expenses represent the most transparent portion of SOC 2 compliance costs. These typically include formal audit fees, which can range from $10,000 to $50,000 depending on organizational complexity. Additional direct costs encompass consultant fees for gap analysis, external security assessments, and the preparation of necessary documentation. Companies often underestimate these upfront expenses, failing to recognize the substantial resources required for comprehensive evidence collection and control documentation.
Indirect expenses frequently prove more challenging to quantify but can significantly impact overall compliance investments. These costs include internal staff time dedicated to compliance preparation, potential productivity losses during the audit process, implementation of new security technologies, and ongoing maintenance of compliance-related infrastructure. Technology teams might need to allocate significant engineering resources to develop and maintain robust security controls, potentially diverting talent from core product development initiatives. Understanding the comprehensive financial implications requires a holistic view that goes beyond simple line-item accounting.
This table contrasts direct versus indirect SOC 2 compliance costs for better budgeting:
Pro Tip - Expense Tracking: Create a dedicated compliance budget spreadsheet that tracks both direct and indirect expenses, categorizing costs by implementation phase, personnel time, and technology investments to gain a clear picture of your total SOC 2 compliance investment.
Hidden Costs and Budgeting Pitfalls
SOC 2 compliance presents a minefield of unexpected financial challenges that can quickly derail even the most carefully planned budgets. Technology firms must develop a sophisticated understanding of the nuanced expenses that extend far beyond traditional compliance calculations.
Hidden resource allocation costs represent a significant financial burden that many organizations fail to anticipate. These expenses manifest through substantial internal staff time dedicated to complex compliance activities, including extensive policy development, evidence collection, and continuous control documentation. Technical teams often discover that compliance preparation consumes exponentially more human capital than initially projected, with key personnel spending hundreds of hours navigating intricate audit requirements instead of focusing on core business initiatives.
Budgeting pitfalls frequently emerge from overlooked operational disruptions caused by the SOC 2 compliance process. Organizations must account for potential productivity losses, temporary reallocation of critical technical resources, and the opportunity costs associated with compliance efforts. Technology companies might experience reduced innovation capacity as engineering teams divert attention from product development to meet stringent security and documentation requirements. Additionally, unexpected technology investments in security infrastructure, monitoring tools, and compliance management platforms can create substantial unplanned expenditures that significantly impact overall budget projections.
Pro Tip - Comprehensive Cost Modeling: Develop a detailed compliance budget model that includes estimated hourly rates for internal staff, potential productivity disruptions, and a 20-30% contingency buffer to account for unforeseen compliance-related expenses.
Strategies to Minimize SOC 2 Expenditure
Successful SOC 2 compliance requires strategic financial planning that balances comprehensive security requirements with budgetary constraints. Technology firms must approach compliance as a calculated investment, implementing targeted strategies to optimize resources and minimize unnecessary expenses.
Cost-effective SOC 2 compliance approaches emphasize the importance of strategic scoping and systematic preparation. Organizations can significantly reduce expenditures by initially focusing solely on the Security trust service criteria, which serves as the foundational requirement. By limiting the initial audit scope and methodically expanding compliance efforts, companies can control costs while maintaining a robust security posture. This approach allows businesses to incrementally invest in compliance, spreading financial resources across multiple budget cycles rather than absorbing a massive upfront expense.
Technical teams can drive down compliance costs through proactive preparation and strategic automation. Implementing continuous monitoring systems, developing standardized documentation processes, and creating repeatable evidence collection mechanisms can dramatically reduce the time and resources required during audit preparation. Advanced organizations leverage technology platforms that enable automated control testing, real-time security monitoring, and streamlined documentation workflows. These technological investments might appear costly initially but ultimately generate substantial long-term savings by reducing manual labor and minimizing potential compliance gaps.
Pro Tip - Strategic Scoping: Begin with a targeted, Security-focused SOC 2 audit, create comprehensive internal documentation templates, and invest in automation tools that support continuous compliance monitoring to minimize both immediate and long-term expenditures.
Simplify Your SOC 2 Compliance Journey and Control Costs with Skypher
SOC 2 compliance can quickly become overwhelming due to hidden costs and extensive manual efforts needed for security questionnaires and documentation. Tech firms face challenges like costly audit fees, resource-draining internal labor, and managing multiple trust service criteria. Skypher addresses these pain points head-on with its AI Questionnaire Automation Tool that significantly cuts down the time spent on responding to complex security reviews.
Why struggle with inefficient processes when you can automate? Skypher’s platform supports over 40 third-party risk management integrations and offers real-time collaboration features to keep your teams aligned and compliant. Accelerate your response times for even hundreds of questions and reduce costly productivity losses during audit preparation by leveraging AI-powered tools designed for complex enterprise environments.
Take control of your SOC 2 compliance costs now by partnering with Skypher. Start streamlining your security questionnaire responses and build a customizable Trust Center that strengthens your cybersecurity posture. Discover how our platform can empower your organization to reduce compliance expense surprises by visiting Skypher and learn more about our AI Questionnaire Automation Tool. Don’t wait until audit time increases your budget pressure—act today to transform your compliance process.
Frequently Asked Questions
What is SOC 2 compliance?
SOC 2 compliance is a cybersecurity framework developed by the AICPA that helps organizations validate their commitment to protecting sensitive customer data through key trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
What factors influence SOC 2 compliance costs for tech firms?
The primary factors influencing SOC 2 compliance costs include the selected audit type, the organization’s complexity, the specific trust service criteria being evaluated, the maturity of existing security controls, and the depth of documentation required to demonstrate compliance.
What are direct and indirect costs associated with SOC 2 compliance?
Direct costs include formal audit fees and consultant fees for gap analysis and documentation preparation. Indirect costs involve internal staff time for compliance preparation, potential productivity losses during the audit, and investments in new security technologies or infrastructure.
How can tech firms minimize SOC 2 compliance expenses?
Tech firms can minimize compliance expenses by strategically scoping their audit, initially focusing on the Security trust service criteria, implementing continuous monitoring systems, standardizing documentation processes, and investing in automation tools to streamline compliance efforts.
Recommended
- Complete Guide to SOC Type II Reports
- Understanding SOC 2 AICPA: Your Guide to Compliance
- Understanding SOC 1 Compliance: Key Concepts Explained
- Understanding SOC II Type 1: What You Need to Know
- Role Of Accountants In Compliance: Why It Matters In UK




.png)
