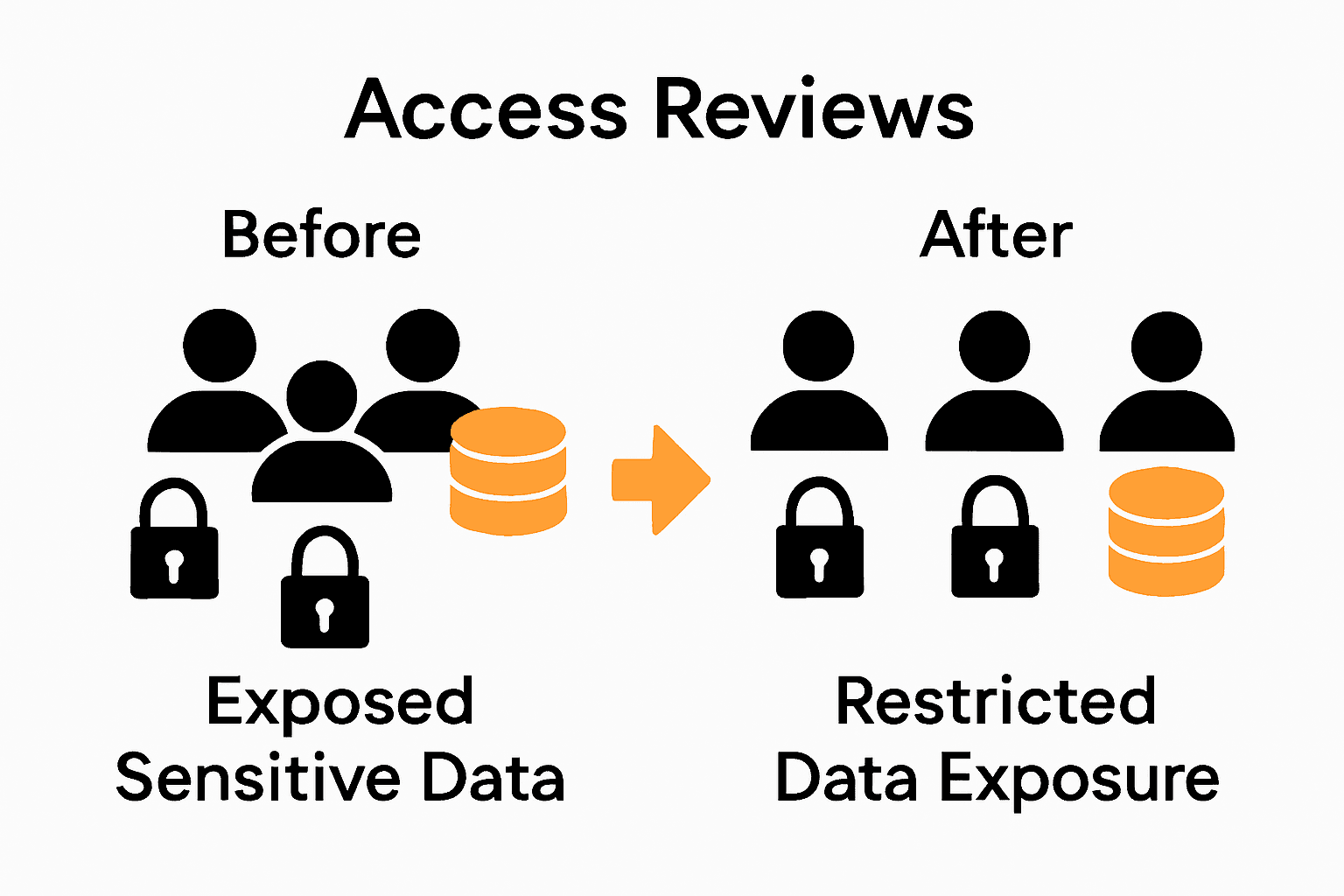
Over 80 percent of american organizations have experienced security risks due to improper user access controls, making robust permission management more crucial than ever. Without careful oversight, sensitive data and mission critical systems can be left exposed, putting operations and reputations at stake. This practical guide offers a straightforward blueprint for building a safer environment by walking you through each step of a proven user access review process.
Table of Contents
- Step 1: Assess Current User Access Permissions
- Step 2: Configure Role-Based Access Controls
- Step 3: Integrate External Identity Providers
- Step 4: Test Access Review Workflow
- Step 5: Document and Validate Review Access Outcomes
Quick Summary
Step 1: Assess Current User Access Permissions
Reviewing user access permissions is a critical security checkpoint that helps protect your organization’s sensitive information and digital infrastructure. According to research from NIST RBAC, systematically examining user access roles ensures that team members have appropriate system permissions aligned with their professional responsibilities.
Start by generating a comprehensive user access inventory that maps each team member to their current system roles and permissions. This involves carefully documenting every individual’s access levels across different platforms, applications, and databases. Look for potential discrepancies like former employees who still retain access, team members with permissions beyond their job requirements, or inconsistent authorization patterns. As recommended by Medium, prioritize conducting regular audits to prevent unauthorized system entry and potential security vulnerabilities.
Quick pro tip: Create a standardized access review template that captures role, current permissions, last login date, and necessary access justification. This systematic approach transforms an often complex process into a clear, actionable workflow. Your next step will involve analyzing these findings and preparing for strategic permission adjustments to strengthen your team’s collaborative security framework.
Step 2: Configure Role-Based Access Controls
Configuring Role-Based Access Controls (RBAC) is your strategic approach to managing user permissions systematically and securely. According to NIST RBAC, RBAC provides a structured method for assigning system access based on specific organizational roles, ensuring that each team member has precisely the permissions required for their job responsibilities.
Begin by mapping out your organizational roles and their corresponding access requirements. As detailed in Cisco’s implementation guide, this process involves creating distinct role definitions that specify exactly what systems and resources each role can access. Develop granular permission sets that range from read-only access to full administrative controls, carefully matching these permissions with job functions.

Break down your roles into clear categories like executive, manager, contributor, and viewer, ensuring each category has carefully defined access boundaries.
Pro tip: Build flexibility into your RBAC framework by creating role hierarchies that allow for easy permission scaling and modification. Your next step will involve validating these configured roles through comprehensive testing and initial user assignment, ensuring your access control strategy provides both robust security and smooth operational workflow.
Step 3: Integrate External Identity Providers
Integrating external identity providers is a strategic approach to streamline user authentication and enhance your organization’s security ecosystem. According to research from ArXiv, managing user identities across multiple services requires careful consideration of trustworthiness and interoperability in complex digital environments.
Start by identifying the specific external identity providers that align with your organization’s security requirements and collaboration needs. The integration process involves establishing secure authentication protocols that allow seamless yet controlled access to your systems. Research suggests ArXiv recommends implementing robust encryption schemes that support multi-organization data sharing while maintaining granular access controls. Carefully map out the authentication workflows, ensuring that each external identity provider undergoes thorough verification and meets your specific security standards. This might include supporting protocols like SAML, OAuth, or OpenID Connect, which enable standardized and secure identity management across different platforms.
Pro tip: Implement a phased integration approach that allows for gradual rollout and comprehensive testing of each external identity provider. Your next step will involve configuring specific authentication rules, testing connection reliability, and establishing continuous monitoring mechanisms to track and validate external user access.
Step 4: Test Access Review Workflow
Testing your access review workflow is a critical step in ensuring the effectiveness and security of your organization’s permission management system. According to NIST RBAC, comprehensive testing validates that access control policies function precisely as intended, preventing potential security vulnerabilities.
Begin by developing a systematic testing strategy that simulates real world scenarios across different user roles and system interactions. As detailed in Cisco’s TrustSec Configuration Guide, this involves creating controlled test environments where you can simulate various access scenarios. Create multiple test user accounts representing different organizational roles, then methodically verify their access levels. Attempt to access resources outside their designated permissions, checking whether the system correctly blocks unauthorized attempts. Pay special attention to edge cases like temporary employees, cross departmental collaborators, and users with complex role assignments.
Pro tip: Develop a comprehensive test matrix that documents expected versus actual access outcomes. Your next step will involve documenting any discrepancies discovered during testing and refining your access control configurations to address potential security gaps.
Step 5: Document and Validate Review Access Outcomes
Documenting and validating access review outcomes is a critical final step in ensuring your organization maintains robust security controls. According to NIST RBAC, maintaining accurate records of user roles and permissions is essential for maintaining comprehensive system security and demonstrating compliance with organizational policies.
Create a comprehensive documentation template that captures detailed information about each access review cycle. As recommended in Cisco’s Unified Computing System Guide, this documentation should include specific details such as user identities, role assignments, access levels, and any modifications made during the review process. Systematically record the rationale behind each access decision, noting any discrepancies discovered during testing and the corresponding corrective actions taken. Implement a standardized scoring or rating system that allows you to quantitatively assess the effectiveness of your access control configurations.
Pro tip: When documenting your access review outcomes, include a section for future recommendations and potential improvements. Your final step will involve presenting these findings to key stakeholders and establishing a recurring review schedule to maintain ongoing security hygiene.
Strengthen Your Team Collaboration with Smarter Access Reviews
Managing access permissions and conducting thorough access reviews can feel overwhelming, especially when security and efficiency are both on the line. This article highlights the need to assess user permissions accurately, configure role-based controls, and validate access workflows to protect sensitive information while maintaining smooth collaboration. Key challenges include preventing unauthorized access, simplifying complex role assignments, and integrating identity providers securely.
Skypher’s AI-driven platform offers powerful solutions that directly address these pain points. With the AI Questionnaire Automation Tool, your team can automate and accelerate security reviews beyond manual audits, ensuring precise access control documentation and faster response times. Benefit from real-time collaboration features and seamless integrations with popular tools like Slack and ServiceNow, so your entire security process stays coordinated and transparent. Skypher’s Custom Trust Center adds an extra layer of confidence by centralizing your security policies and audit results in one secure space.
Experience how optimized access reviews can transform your team’s security practices. Visit https://skypher.co today to explore our platform and start automating your security questionnaire responses with unmatched speed and accuracy. Take control of your access management challenges and enhance your team collaboration now.
Frequently Asked Questions
How can I assess current user access permissions for my team?
Begin by generating a comprehensive user access inventory that documents each team member’s roles and permissions across various systems. Review for discrepancies such as former employees with access or users having permissions beyond their job requirements, and aim to conduct this audit at least quarterly.
What steps should I follow to configure Role-Based Access Controls (RBAC)?
Start by mapping out the organizational roles and the permissions associated with each. Define clear role categories and establish permissions that align with job functions, ensuring that each role only has the access they need to perform their duties effectively.
How do I integrate external identity providers for team collaboration?
Identify the external identity providers that suit your organization’s needs and establish secure authentication protocols to manage access. Implement protocols like SAML or OAuth and ensure that each provider’s workflows are thoroughly verified to maintain security while enabling seamless user access.
What is the best way to test my access review workflow?
Develop a systematic testing strategy that simulates real-world scenarios for different user roles. Create controlled test accounts, then check if these accounts can access resources appropriately, noting any discrepancies for further adjustments in your access control setup.
How can I document and validate the outcomes of my access review?
Create a detailed documentation template capturing information about user identities, roles, access levels, and any changes made during reviews. Record your findings systematically and include potential recommendations for improvement, ensuring ongoing security monitoring.
Recommended
- Security Questionnaires Automation Software
- 7 Essential Steps for a Security Compliance Checklist
- AI-Powered Security Questionnaires Automation - Skypher
- Features
- Understanding Managing Remote Teams: Key Concepts Explained|CS
- Understanding User Access Management for Businesses - TECHTRON





