Every security questionnaire review brings fresh challenges for CISOs and compliance officers as regulations multiply and technologies change at a rapid pace. The pressure to manage compliance risk is not just about avoiding penalties, but also about protecting trust and business continuity in highly regulated sectors like finance and technology. This guide spotlights the complexity of compliance risk and offers practical approaches to help you safeguard your organization’s reputation while streamlining your security processes.
Table of Contents
- Defining Compliance Risk In Modern Business
- Key Types And Categories Of Compliance Risk
- Major Drivers And Sources In Tech And Finance
- Real-World Implications For Security Reviews
- Effective Management And Mitigation Strategies
Key Takeaways
Defining Compliance Risk in Modern Business
Compliance risk represents the potential legal, financial, and reputational exposure organizations face when failing to meet regulatory requirements, internal policies, or established standards. At its core, compliance risk involves the likelihood of facing sanctions, penalties, or significant operational disruptions due to non-adherence to external and internal guidelines.
Businesses encounter compliance risks across multiple dimensions, which can be categorized into several critical areas:
- Regulatory Compliance: Adherence to government and industry-specific regulations
- Financial Compliance: Following accounting standards and financial reporting requirements
- Operational Compliance: Meeting internal policy standards and operational guidelines
- Ethical Compliance: Maintaining integrity and preventing fraudulent activities
Compliance risk management has become increasingly complex in today’s globally interconnected business environments. Organizations must proactively identify, assess, and mitigate potential risks to maintain their operational integrity and protect their reputation.
The consequences of non-compliance can be substantial. Financial penalties, legal actions, reputational damage, and potential business disruptions make compliance risk management a critical strategic priority for modern enterprises. Companies must develop robust frameworks that enable continuous monitoring, rapid response, and adaptive risk management strategies.
Pro tip: Implement a comprehensive compliance risk assessment framework that includes regular audits, employee training, and real-time monitoring to effectively mitigate potential organizational vulnerabilities.
Key Types and Categories of Compliance Risk
Compliance risks encompass a complex landscape of potential organizational vulnerabilities that extend far beyond traditional regulatory frameworks. Modern businesses must navigate an increasingly intricate network of potential risk categories that demand sophisticated, proactive management strategies.
Global compliance risk surveys reveal several critical categories of compliance risk that organizations must systematically address:
- Anti-Corruption Risks: Preventing bribery, unethical payments, and improper business practices
- Third-Party Management Risks: Ensuring vendors and partners meet compliance standards
- Cybersecurity Compliance Risks: Protecting digital assets and maintaining data security protocols
- Environmental, Social, and Governance (ESG) Risks: Adhering to sustainability and ethical business standards
- Data Privacy Risks: Protecting sensitive information and maintaining regulatory compliance
- Financial Reporting Risks: Ensuring accurate and transparent financial disclosures
Each compliance risk category requires a nuanced approach that goes beyond simple checklist management. Organizations must develop integrated risk management frameworks that can dynamically adapt to evolving regulatory landscapes and emerging technological challenges.
The interconnected nature of modern compliance risks demands a holistic strategy. Companies must invest in continuous employee training, robust technological infrastructure, and agile risk assessment methodologies to effectively mitigate potential vulnerabilities across multiple risk domains.

Here is a summary contrasting key compliance risk categories and their distinctive business impacts:
Pro tip: Develop a comprehensive compliance risk mapping system that categorizes and prioritizes risks based on potential impact, likelihood of occurrence, and organizational readiness.
Major Drivers and Sources in Tech and Finance
Compliance risk in technology and financial sectors has become increasingly complex, driven by rapid technological innovations and evolving regulatory landscapes. Technological disruption has fundamentally transformed how organizations approach risk management, creating unprecedented challenges for compliance professionals.
Regulatory compliance challenges in tech and finance are primarily fueled by several critical drivers:
- Emerging Technologies: Blockchain, artificial intelligence, and cloud computing
- Cybersecurity Threats: Increasingly sophisticated digital attack vectors
- Data Privacy Regulations: Stringent global data protection requirements
- Third-Party Risk Management: Complex vendor and partnership ecosystems
- Digital Transformation: Accelerated technological adoption across industries
- Regulatory Complexity: Continuously changing legal and compliance frameworks
Financial institutions and technology companies must develop adaptive strategies that can rapidly respond to these dynamic risk environments. The intersection of technological innovation and regulatory oversight demands unprecedented levels of organizational agility and proactive risk management.

The landscape of compliance risk is fundamentally reshaped by the continuous evolution of digital technologies. Organizations must invest in robust governance frameworks, advanced risk monitoring technologies, and comprehensive employee training programs to effectively navigate these complex challenges.
Pro tip: Create a cross-functional compliance task force that combines technological expertise, legal knowledge, and strategic risk management to develop holistic compliance strategies.
Real-World Implications for Security Reviews
Security reviews have become a critical component of organizational risk management, transforming from routine compliance exercises to strategic defensive mechanisms. Compliance frameworks now play a pivotal role in protecting organizations against sophisticated cyber threats and potential operational vulnerabilities.
Compliance security frameworks significantly impact cybersecurity by addressing multiple critical dimensions:
- Legal Compliance: Meeting regulatory standards like GDPR, HIPAA, and PCI DSS
- Threat Mitigation: Proactively identifying and addressing potential security risks
- Incident Response: Developing structured approaches to managing security breaches
- Risk Assessment: Continuously evaluating organizational vulnerabilities
- Data Protection: Safeguarding sensitive information across digital ecosystems
- Operational Resilience: Maintaining business continuity during potential security challenges
Organizations must recognize that security reviews are no longer just checkbox activities but strategic imperatives that directly influence operational integrity and organizational reputation. The dynamic nature of cyber threats demands continuous adaptation and sophisticated risk management approaches.
The complexity of modern security reviews requires a holistic approach that integrates technological capabilities, human expertise, and robust governance frameworks. Companies must invest in advanced monitoring technologies, comprehensive employee training, and agile risk assessment methodologies to effectively navigate the increasingly intricate landscape of cybersecurity compliance.
Pro tip: Implement a dynamic, risk-based security review process that incorporates continuous monitoring, regular vulnerability assessments, and adaptive response mechanisms.
Effective Management and Mitigation Strategies
Managing compliance risk requires a comprehensive, strategic approach that goes beyond traditional defensive mechanisms. Compliance strategies must be dynamic, proactive, and deeply integrated into an organization’s core operational framework.
Effective mitigation strategies involve a multi-dimensional approach that addresses various organizational vulnerabilities:
- Regular Risk Assessments: Conducting comprehensive evaluations of potential compliance risks
- Employee Training: Developing robust educational programs on compliance standards
- Technology Integration: Leveraging automation and advanced analytics for risk monitoring
- Third-Party Management: Implementing rigorous vendor compliance screening processes
- Continuous Improvement: Creating adaptive frameworks that evolve with regulatory changes
- Strategic Alignment: Embedding compliance into core business functions
Successful compliance risk management requires more than just implementing a set of procedures. Organizations must cultivate a culture of compliance that permeates every level of the organization, transforming risk management from a defensive posture to a strategic competitive advantage.
The most effective mitigation strategies embrace technological innovation, human expertise, and adaptive governance frameworks. Companies must invest in advanced monitoring tools, comprehensive training programs, and agile risk assessment methodologies that can quickly respond to emerging regulatory and technological challenges.
This table compares popular mitigation strategies and their value for compliance risk management:
Pro tip: Develop a cross-functional compliance task force that combines technological expertise, legal knowledge, and strategic risk management to create holistic, adaptive compliance strategies.
Streamline Your Security Reviews with AI-Powered Compliance Solutions
Compliance risk demands precise, agile management to protect your organization against evolving regulatory and cybersecurity challenges. If navigating complex security questionnaires and maintaining continuous compliance feels overwhelming, Skypher offers a powerful solution. Our AI Questionnaire Automation Tool drastically reduces the time and effort needed to complete extensive security reviews while improving accuracy and collaboration across your team.
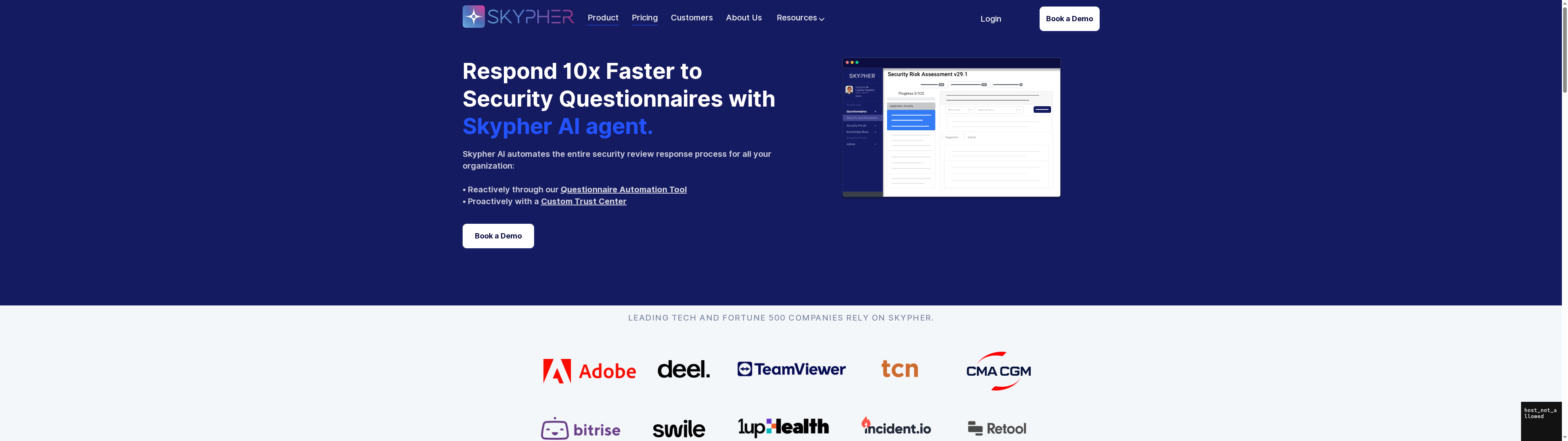
Ready to transform your compliance process? Discover how Skypher’s AI Questionnaire Automation Tool, integrated with over 40 third-party risk management platforms, can accelerate your security reviews and strengthen your operational resilience. Explore our Custom Trust Center and secure continuous compliance with full visibility and control. Visit Skypher today and take the first step toward simplifying your compliance risk management with cutting-edge AI technology.
Frequently Asked Questions
What is compliance risk and why is it important for businesses?
Compliance risk refers to the potential legal, financial, and reputational exposure that businesses face if they fail to meet regulatory requirements and internal policies. Managing compliance risk is crucial to prevent sanctions, penalties, and operational disruptions.
How do compliance risks impact cybersecurity measures within organizations?
Compliance risks significantly impact cybersecurity by dictating the necessary protective measures against data breaches and legal standards like GDPR and HIPAA. Effective compliance frameworks help organizations identify vulnerabilities and strengthen their security posture.
What are some common categories of compliance risks that businesses face?
Common categories include anti-corruption risks, third-party management risks, cybersecurity compliance risks, environmental, social, and governance (ESG) risks, data privacy risks, and financial reporting risks. Each category requires a tailored approach to management.
What strategies can organizations implement to mitigate compliance risks?
Organizations can mitigate compliance risks by conducting regular risk assessments, providing employee training, integrating technology for monitoring, managing third-party compliance, and continually updating their compliance frameworks to adapt to new regulations.
Recommended
- Automated Compliance: Transforming Security Reviews
- Complete Guide to Software Compliance Software
- 7 Essential Steps for a Security Compliance Checklist
- Understanding the HIPAA Security Rule for Businesses
- GDPR Compliance in Testing: Practical Guide for Marketers 2025
- Website Security: Safeguarding Brands and Customer Trust
- Fifty1 Consulting




