Managing security questionnaires can quickly become overwhelming when every organization faces different risks, clients demand rapid responses, and your team is spread across locations. It is easy to get lost in endless drafts, miscommunications, and uncertainty about whether you are truly protecting sensitive information. The right approach will not only reduce stress but transform your security process into a strategic advantage.
You are about to discover proven methods that make automated secure question management collaborative, accurate, and actionable. These insights cover everything from crafting clear questions to using AI and enabling real-time teamwork. With practical steps backed by both the latest research and real-world success, you will find new ways to elevate your organization’s security—and gain peace of mind that your defenses are always a step ahead.
Table of Contents
- Understand The Core Of Secure Questions
- Choose An AI-Driven Automation Tool
- Integrate With Trusted Third-Party Platforms
- Enable Real-Time Team Collaboration
- Customize Your Trust Center For Clients
- Utilize Multiformat Questionnaire Support
- Ensure Enterprise-Grade Security And Compliance
Quick Summary
1. Understand the Core of Secure Questions
Secure questions form the critical foundation of organizational risk assessment and cybersecurity strategy. At their core, these targeted inquiries help companies evaluate potential vulnerabilities and establish robust defense mechanisms.
The primary purpose of secure questions is to systematically probe an organization’s security landscape. These are not random queries but strategically designed investigations that reveal potential weak points in systems, processes, and human interactions.
Key characteristics of effective secure questions include:
- Specificity in identifying potential security risks
- Clarity that allows precise and actionable responses
- Alignment with organizational security frameworks
- Capability to uncover hidden operational vulnerabilities
Research on secure questions demonstrates that well-constructed questions can dramatically improve an organization’s risk management approach.
By developing questions that target critical areas like data protection protocols, access management, and incident response procedures, companies can create a comprehensive security assessment framework. These questions should not just be technical but also consider human factors and potential behavioral risks.
Effective secure questions transform abstract security concerns into concrete, actionable intelligence.
Successful secure questions require a deep understanding of your organization’s unique technological ecosystem and potential threat landscapes. This means tailoring questions to specific departmental needs while maintaining a holistic view of overall security posture.
Pro tip: Create a dynamic question library that evolves with emerging technological threats and organizational changes, ensuring your secure question strategy remains adaptive and relevant.
2. Choose an AI-Driven Automation Tool
Picking the right AI-driven automation tool can transform your secure question generation from a time-consuming manual process to a streamlined strategic operation. Modern AI technologies now enable organizations to dramatically reduce administrative overhead while maintaining rigorous security standards.
AI-powered tools leverage advanced technologies to generate precise and contextually relevant questions that adapt to your organization’s specific security landscape. These sophisticated systems go beyond simple template matching by understanding nuanced security contexts.
Key features to look for in an AI-driven automation tool include:
- Natural language processing capabilities
- Machine learning adaptability
- Comprehensive security knowledge base
- Real-time validation frameworks
- Customizable question generation
- Integration with existing security platforms
AI-powered recommendation engines demonstrate remarkable potential in generating high-quality, guideline-compliant security questions with minimal human intervention.
Implementing an AI automation tool requires careful evaluation of your organization’s unique security needs. Consider factors like scalability, ease of integration, and the tool’s ability to learn and adapt to your specific threat landscape.
The right AI tool transforms security questionnaires from a compliance checkbox into a strategic intelligence gathering mechanism.
When selecting an AI-driven automation tool, prioritize solutions that offer human-in-the-loop validation. This ensures that while AI generates questions, human expertise provides critical oversight and refinement.
Pro tip: Conduct a pilot test with multiple AI automation tools to compare their performance and alignment with your organization’s specific security requirements before making a final selection.
3. Integrate with Trusted Third-Party Platforms
Successful secure question automation requires seamless integration with trusted third-party platforms that enhance your organization’s security ecosystem. Strategic platform integration transforms isolated security processes into a comprehensive risk management network.
Trusted third-party platforms provide critical infrastructure for expanding and validating your secure question automation strategy. These platforms offer specialized capabilities that complement your internal security frameworks and create more robust assessment mechanisms.
Key considerations for platform integration include:
- Comprehensive API connectivity
- Robust authentication protocols
- Real-time data synchronization
- Compliance with industry security standards
- Scalable integration architectures
- Multi-factor verification capabilities
When evaluating potential third-party platforms, thoroughly assess vendor risk management to ensure alignment with your organizational security requirements. Look for platforms that offer transparent security documentation and demonstrate a proven track record of reliability.
Effective platform integration requires more than technical compatibility. You need solutions that can seamlessly communicate across different systems while maintaining the highest standards of data protection and confidentiality.
Platform integration is not just about connection it is about creating a unified security intelligence network.
Organizations should prioritize platforms that offer flexible integration options and support advanced security protocols. This approach enables dynamic risk assessment and provides comprehensive visibility into potential vulnerabilities.
Pro tip: Conduct thorough due diligence by requesting detailed security compliance reports and performing comprehensive integration testing before finalizing any third-party platform partnership.
4. Enable Real-Time Team Collaboration
Real-time team collaboration transforms secure question automation from a fragmented process into a synchronized intelligence-gathering mechanism. By enabling instant communication and collaborative workflows, organizations can dramatically improve their security response efficiency.
Modern collaboration tools provide unprecedented connectivity for security teams, allowing multiple stakeholders to contribute, review, and validate secure questionnaire responses simultaneously. This approach breaks down traditional communication barriers and accelerates decision-making.
Key benefits of real-time collaboration include:
- Instant feedback mechanisms
- Synchronized document editing
- Dynamic task assignment
- Reduced response preparation time
- Enhanced cross-departmental communication
- Immediate error detection and correction
Real-time collaborative environments demonstrate significant improvements in response quality by enabling immediate monitoring and feedback from subject matter experts.
Successful implementation requires selecting collaboration platforms that integrate seamlessly with your existing security infrastructure. Look for tools that offer granular access controls, comprehensive audit trails, and robust encryption protocols.
Effective team collaboration transforms security questionnaires from isolated tasks into strategic intelligence gathering opportunities.
Organizations should prioritize platforms that support multiple communication channels and provide contextual collaboration features. This ensures that every team member can contribute expertise while maintaining strict security protocols.
Pro tip: Establish clear collaboration guidelines and role-based access permissions before implementing real-time collaboration tools to ensure smooth and secure team interactions.
5. Customize Your Trust Center for Clients
A customized Trust Center transforms security documentation from a static compliance artifact into a dynamic client engagement tool. By tailoring your security resources to specific client needs, you create a powerful mechanism for building trust and accelerating sales cycles.
Customization is more than just changing colors or adding logos. Intelligent Trust Center design requires strategic segmentation of security content that speaks directly to different client profiles and industry requirements.
Key customization strategies include:
- Creating industry-specific documentation sets
- Implementing role-based access controls
- Developing dynamic content filters
- Supporting multiple language options
- Enabling granular document sharing
- Configuring NDA-gated content access
Custom trust center strategies enable organizations to organize security content through intelligent tagging and targeted resource sharing.
The most effective Trust Centers go beyond simple document repositories. They become interactive platforms that anticipate and address client security concerns before they are even raised. This proactive approach demonstrates your commitment to transparency and builds confidence.
A well-designed Trust Center is not just a document library it is a strategic communication platform.
Organizations should view their Trust Center as a living ecosystem that evolves with changing client expectations and regulatory landscapes. Regular updates and client feedback integration are crucial for maintaining relevance and effectiveness.
Pro tip: Implement analytics tracking within your Trust Center to understand which documents clients access most frequently and use these insights to continuously refine your security content strategy.
6. Utilize Multiformat Questionnaire Support
Multiformat questionnaire support represents a game changing approach to secure question management. By supporting diverse document formats and question types, organizations can dramatically enhance their security assessment capabilities.
The ability to process and transform questionnaires across different formats provides unprecedented flexibility in security assessments. Modern automation tools can seamlessly convert and adapt questionnaire content from PDFs, text files, images, and other sources.
Key advantages of multiformat support include:
- Rapid document ingestion
- Automatic format conversion
- Reduced manual data entry
- Enhanced accuracy
- Improved response consistency
- Comprehensive content extraction
Multiformat questionnaire technologies enable organizations to generate adaptive surveys that accommodate complex security evaluation requirements.
Successful implementation requires selecting platforms with robust parsing capabilities. Look for solutions that can handle complex document structures and extract nuanced information across various input formats.
Multiformat support transforms rigid questionnaire processes into dynamic intelligence gathering mechanisms.
Organizations should prioritize tools that not only support multiple formats but also provide intelligent content analysis. This means going beyond simple text extraction to understanding context and potential security implications.
Pro tip: Conduct periodic audits of your multiformat support capabilities to ensure your automation tools can handle emerging document types and complex security questionnaire structures.
7. Ensure Enterprise-Grade Security and Compliance
Enterprise-grade security and compliance represent the gold standard for protecting organizational information and maintaining regulatory integrity. This critical approach transforms security questionnaires from simple checklists into strategic risk management tools.
Comprehensive security frameworks demand more than superficial compliance measures. They require sophisticated, intelligent systems that can adapt to complex regulatory landscapes and organizational nuances.
Key elements of enterprise-grade security include:
- Role-based access controls
- Comprehensive audit trails
- Advanced encryption protocols
- Continuous compliance monitoring
- Adaptive risk assessment mechanisms
- Regulatory framework alignment
Enterprise-grade security platforms leverage advanced AI models to generate context-aware, accurate responses that meet rigorous industry standards.
Successful implementation requires a holistic approach that integrates technological solutions with robust organizational policies. This means selecting tools that not only automate processes but also provide granular control and comprehensive reporting capabilities.
Enterprise security is not a destination it is a continuous, adaptive journey of protection and optimization.
Organizations must prioritize platforms that offer seamless integration with existing security infrastructure while providing flexibility to evolve with emerging regulatory requirements.
Pro tip: Conduct quarterly comprehensive reviews of your security automation tools to ensure they remain aligned with the latest regulatory standards and technological advancements.
Below is a comprehensive table summarizing key strategies and implementations related to security question automation and cybersecurity enhancements discussed throughout the article.
Unlock Seamless Secure Question Automation with Skypher
The article highlights the challenges organizations face in streamlining secure question processes while ensuring enterprise-grade security, real-time collaboration, and multiformat questionnaire support. If you are struggling with managing complex security questionnaires efficiently or integrating with multiple third-party platforms, Skypher offers a tailored solution designed to meet those exact needs. Our AI-driven automation tool not only accelerates the response process but also enhances accuracy and transparency across your teams.
Skypher’s platform supports:
- AI-powered generation and rapid answering of hundreds of security questions
- Integration with over 30 risk management platforms like ServiceNow and OneTrust
- Real-time collaboration features including Slack and Microsoft Teams integrations
- Customizable Trust Center to build client confidence and reduce sales cycle times
- Support for all questionnaire formats and multilingual content handling
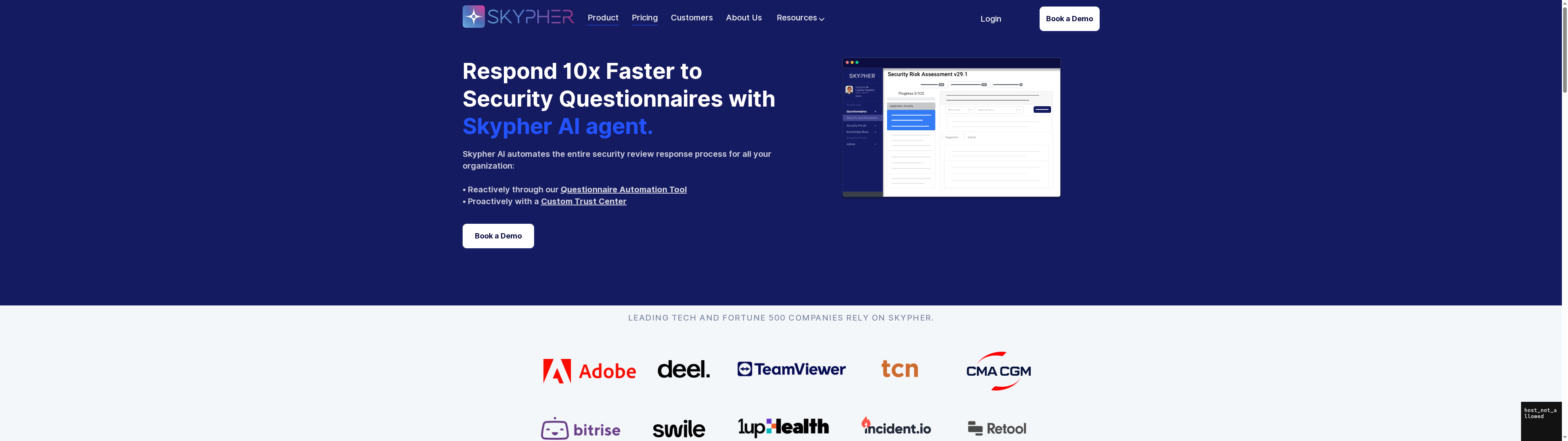
Experience how Skypher transforms secure questions from a cumbersome task into a strategic advantage. Visit Skypher now and discover how our questionnaire automation tool can help your organization comply faster, collaborate smarter, and build stronger client trust today. Start your journey toward effortless security reviews and improve operational productivity by learning more on our landing page. For added insight, explore our API integrations that connect your ecosystem seamlessly.
Frequently Asked Questions
How can I create effective secure questions for my organization?
To create effective secure questions, focus on specificity and clarity. Identify critical areas such as data protection and access management, and tailor questions to reveal potential vulnerabilities. Review and adapt your questions regularly to keep pace with emerging threats.
What features should I look for in an AI-driven automation tool for secure question generation?
When selecting an AI-driven automation tool, prioritize features like natural language processing and machine learning adaptability. Ensure the tool can generate contextually relevant questions and integrates well with your existing security frameworks. Test multiple tools to find the best fit for your specific security needs.
How can I integrate secure question automation with third-party platforms effectively?
To integrate secure question automation with third-party platforms, ensure you have robust API connectivity and authentication protocols in place. Focus on platforms that support real-time data synchronization and comply with industry security standards. Conduct thorough testing to confirm seamless communication between your systems.
What are the benefits of enabling real-time team collaboration in secure question processes?
Enabling real-time team collaboration allows for instant feedback and synchronized document editing, which greatly improves response times. Encourage teams to use collaboration tools that facilitate dynamic task assignments and immediate error detection to enhance overall security effectiveness.
How can I customize my Trust Center to better serve clients?
To customize your Trust Center, create industry-specific documentation and implement role-based access controls. Develop dynamic content filters based on client needs and preferences, and ensure it remains an interactive platform that addresses security concerns proactively. Regularly update the content to reflect changing client expectations.
Why is multiformat questionnaire support important for secure question management?
Multiformat questionnaire support allows organizations to process questionnaires in various formats, improving flexibility and accuracy in assessments. Use platforms that can automatically convert multiple document types and minimize manual data entry to enhance the efficiency and consistency of your security evaluations.




