Most American companies underestimate just how much inconsistent security skills can leave their software exposed. With cyber threats growing more sophisticated each year, even one gap in a team’s secure coding knowledge puts critical data at risk. This guide breaks down proven strategies to help American development teams close those gaps, from skill assessments to collaborative solutions, so you can create a culture of security that stands up against evolving risks.
Table of Contents
- Step 1: Assess Current Team Security Skills
- Step 2: Implement Secure Coding Standards
- Step 3: Leverage Automated Training Tools
- Step 4: Foster Team Collaboration on Secure Practices
- Step 5: Verify Security Coding Effectiveness
Quick Summary
Step 1: Assess Current Team Security Skills
Assessing your development team’s security skills is a critical first step in building a robust security culture. This process involves systematically evaluating your team’s current capabilities, identifying knowledge gaps, and creating targeted improvement strategies.
Start by conducting a comprehensive security skills assessment that measures your team’s practical understanding of secure coding principles. Research indicates that many organizations struggle with developer security awareness, with studies showing significant variations in security skill levels across teams. A structured evaluation should include technical assessments, practical coding challenges, and scenario-based tests that examine how developers respond to potential security vulnerabilities.
Key assessment components should include reviewing past code repositories, conducting individual skill interviews, and administering standardized security knowledge tests. Pay special attention to how team members handle authentication mechanisms, input validation, and secure data handling. The goal is not to criticize but to create a clear roadmap for skill development that transforms potential weaknesses into strengths.
One critical warning: avoid making these assessments feel punitive. Frame the evaluation as a collaborative growth opportunity that helps every team member become a more effective and security-conscious developer. When team members understand that the assessment is about empowerment rather than criticism, they are more likely to engage genuinely and demonstrate their true capabilities.
Once you have completed the assessment, you will be prepared to design targeted training programs that address specific skill gaps and reinforce secure coding practices across your entire development team.
Step 2: Implement Secure Coding Standards
Implementing secure coding standards transforms abstract security concepts into actionable guidelines that protect your software development ecosystem. This crucial phase establishes a comprehensive framework that systematically reduces vulnerabilities and creates a consistent security approach across your entire development team.
Begin by developing comprehensive secure coding guidelines that cover critical security domains. Effective standards should address input validation, authentication mechanisms, error handling, and data protection protocols. Secure coding practices require meticulous attention to details such as sanitizing user inputs, implementing robust authentication checks, and creating secure communication channels.
Establish a multi-tier implementation strategy that includes mandatory training sessions, code review processes, and automated security scanning tools. Create clear documentation that outlines specific coding requirements, providing concrete examples of secure versus vulnerable code patterns. Integrate these standards directly into your development workflow, ensuring that every team member understands and can practically apply these security principles.

One critical warning emerges from security research: standards are only effective when consistently enforced. Develop a mechanism for ongoing compliance tracking and create a culture that views secure coding not as an obstacle but as an integral part of quality software development. Regular workshops, peer code reviews, and continuous learning opportunities will help embed these standards into your team’s daily practice.
As you complete this implementation, you will have transformed security from an abstract concept into a tangible, actionable set of guidelines that protect your software development process from potential vulnerabilities.
Step 3: Leverage Automated Training Tools
Leveraging automated training tools transforms security education from theoretical concepts to practical skill development, enabling your development team to proactively identify and mitigate potential vulnerabilities. This strategic approach integrates cutting-edge technological solutions to enhance your team’s security awareness and technical capabilities.
Implement static code analysis tools that systematically scan your codebase for potential security weaknesses. These advanced technologies help bridge knowledge gaps by automatically detecting vulnerabilities that developers might inadvertently introduce during coding. Security scanning technologies can identify critical issues such as improper input validation, authentication flaws, and potential data exposure points before they become serious security risks.
Design a comprehensive training ecosystem that combines automated tools with interactive learning modules. Select platforms that offer real-time feedback, contextual learning experiences, and hands-on simulation exercises. Configure these tools to provide personalized learning paths based on individual developer skill levels, ensuring that each team member receives targeted training that addresses their specific knowledge gaps.
One critical warning: automated tools are powerful but not infallible. While these technologies provide exceptional insights, they cannot replace human expertise and critical thinking. Encourage your team to view these tools as collaborative partners in security enhancement rather than absolute arbiters of code quality.
As you complete this implementation, you will have established a dynamic, intelligent training environment that continuously adapts to emerging security challenges and empowers your developers to write more secure, resilient code.
Step 4: Foster Team Collaboration on Secure Practices
Fostering team collaboration in secure coding practices transforms individual knowledge into a collective security strategy that protects your entire organization. This critical step involves creating an environment where security becomes a shared responsibility and collaborative effort across your development team.
Establish clear collaboration frameworks that promote transparent communication and shared accountability for security outcomes. Proactive risk management approaches can help teams develop a unified understanding of security challenges, enabling more effective problem solving and knowledge sharing. Implement regular collaborative sessions where team members can discuss potential vulnerabilities, share insights, and collectively develop strategies for addressing complex security scenarios.
Create a robust feedback mechanism that rewards collaborative security efforts and encourages open dialogue about potential risks. Design performance metrics that recognize not just individual technical achievements but also contributions to team security awareness. Develop shared documentation platforms where developers can log security observations, discuss potential improvements, and maintain a living knowledge base that evolves with emerging threats.
One critical warning emerges from collaborative research: transparency requires psychological safety. Ensure your team understands that discussing security challenges is about collective improvement, not individual blame. Cultivate an environment where team members feel comfortable raising concerns and sharing potential vulnerabilities without fear of negative repercussions.
As you complete this collaborative transformation, you will have built a resilient security culture where knowledge flows freely, risks are identified quickly, and your team becomes a unified defense mechanism against potential security threats.
Step 5: Verify Security Coding Effectiveness
Verifying security coding effectiveness transforms your development process from reactive defense to proactive protection. This critical phase ensures that your security standards are not just documented but genuinely implemented and producing meaningful results across your development ecosystem.
Code review mechanisms represent the cornerstone of comprehensive security validation. Implement rigorous evaluation processes that systematically examine code for potential vulnerabilities, analyzing not just syntax but the underlying security implications of each implementation. Advanced code analysis techniques can help identify complex security weaknesses that might escape traditional review methods, utilizing sophisticated algorithmic approaches to detect potential risks.
Develop a multi layered verification strategy that combines automated scanning tools, manual code reviews, and periodic security assessments. Create comprehensive evaluation frameworks that score code not just on functional performance but on security resilience. Design metrics that track security improvements over time, providing clear visibility into your team’s evolving security capabilities and highlighting areas requiring additional focus or training.
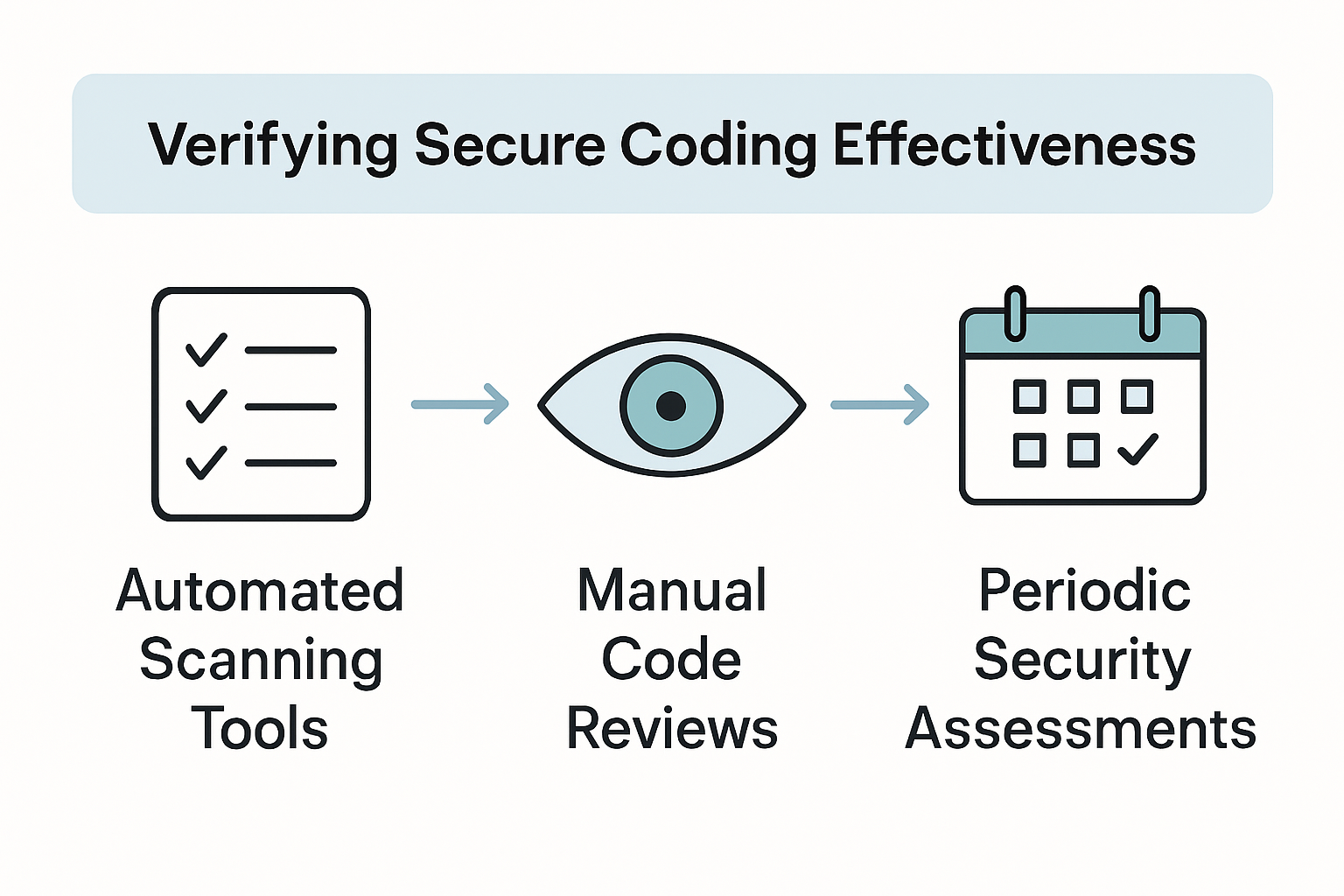
One critical warning emerges from security research: verification is an ongoing process. Do not treat security assessment as a one time event. Continuous monitoring and repeated evaluations are essential to maintain a robust defense against emerging threats and evolving attack vectors.
As you complete this verification process, you will have transformed security from a theoretical concept into a measurable, actionable component of your software development lifecycle.
Elevate Your Secure Development Through Automated Security Collaboration
Building a strong security culture requires not only assessing and improving your team’s coding skills but also streamlining collaboration and verifying security effectiveness. The challenges of implementing secure coding standards and maintaining ongoing verification can leave teams overwhelmed and vulnerable. Skypher’s AI-driven Questionnaire Automation Tool is designed to simplify complex security workflows, helping you accelerate security reviews, automate risk assessments, and foster real-time collaboration among team members.
Take control of your secure development journey today by leveraging Skypher’s integrations with leading platforms like ServiceNow and Slack, enabling seamless communication and efficient security questionnaire responses. With features such as a customizable Trust Center and 24/7 enterprise support, Skypher empowers your organization to reduce time spent on security processes while enhancing accuracy and compliance. Don’t wait for security challenges to escalate—explore how Skypher can transform your security coding practices and operational productivity now at Skypher.
Frequently Asked Questions
What is the first step in Security Coding Training for my development team?
Assessing your development team’s security skills is the first critical step. Conduct a comprehensive security skills assessment to identify knowledge gaps and create targeted strategies for improvement.
How can I implement secure coding standards effectively?
To effectively implement secure coding standards, develop comprehensive guidelines that cover key security domains such as input validation and authentication mechanisms. Ensure you provide training sessions, document specific coding requirements, and integrate these standards into your development workflow.
What types of automated training tools should I consider for security coding?
Consider using static code analysis tools that scan your codebase for potential security weaknesses. Look for tools that offer real-time feedback and personalized learning paths to ensure each team member can develop their skills effectively.
How can I foster collaboration among my development team regarding secure coding practices?
Create clear collaboration frameworks that promote open communication and shared accountability for security outcomes. Implement regular collaborative sessions where team members can discuss vulnerabilities and work together on security challenges.
What should be included in the verification process for security coding effectiveness?
The verification process should include rigorous code reviews, automated scanning tools, and periodic security assessments. Establish metrics to track security improvements over time and ensure ongoing evaluation to continuously strengthen security measures.
How often should I reassess my development team’s security skills?
You should reassess your development team’s security skills regularly, ideally every 6 to 12 months. This ongoing process helps to maintain and enhance their security capabilities in reaction to evolving threats.
Recommended
- Business | Security Questionnaire Automation | Skypher
- Complete Guide to Data Security Best Practices
- 7 Effective Security Questions Examples for Your Business
- Understanding SOC 2 AICPA: Your Guide to Compliance
- Understanding Online Payment Security: Essential Insights|CS
- Understanding Cybersecurity Awareness Training - TECHTRON





