Cybersecurity threats are growing more unpredictable each year, and businesses are scrambling to keep up. Yet while most companies pour money into firewalls and anti-virus tools, over 60 percent of data breaches still exploit gaps in governance, risk, and compliance frameworks. This flips the script—because the real edge in 2025 is not just better technology but smarter, integrated GRC strategies that turn security compliance into a business advantage.
Table of Contents
- Understanding Cybersecurity Grc Frameworks
- Key Benefits And Importance For Businesses
- Best Practices For Building An Effective Grc Program
- Cybersecurity Grc Trends And Future Insights
Quick Summary
| Takeaway | Explanation |
|---|---|
| Integrate GRC with Business Goals | Successful GRC frameworks must align cybersecurity practices with overall business strategies for effective outcomes. |
| Emphasize Continuous Monitoring | Regular surveillance of security environments is crucial for adapting to new threats and vulnerabilities. |
| Leverage Advanced Technologies | Incorporating AI and automation can enhance risk management and compliance processes significantly. |
| Build Strong Governance Foundations | Establish clear policies and defined roles to ensure accountability in cybersecurity management. |
| Adopt a Proactive Compliance Approach | Organizations should view compliance as a dynamic capability rather than a static obligation. |
Understanding Cybersecurity GRC Frameworks
Cybersecurity Governance, Risk, and Compliance (GRC) frameworks provide organizations with structured approaches to managing their security posture, aligning technological capabilities with strategic business objectives. These frameworks offer comprehensive methodologies for identifying, assessing, and mitigating cybersecurity risks while ensuring regulatory compliance.
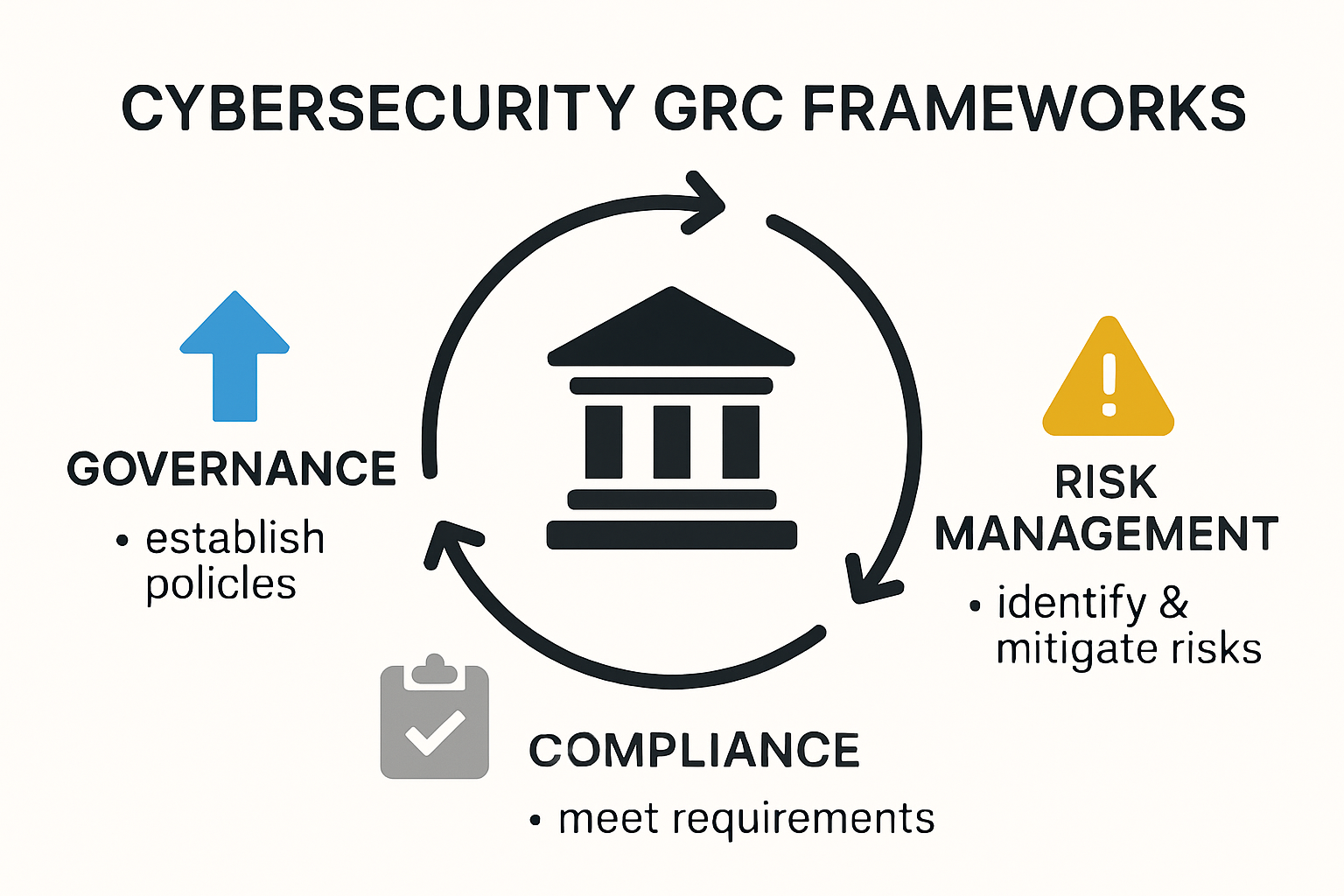
Core Components of Cybersecurity GRC Frameworks
At the heart of effective cybersecurity GRC lie three critical interconnected elements. Governance establishes the strategic direction and oversight mechanisms for an organization’s security practices. This involves creating clear policies, defining roles and responsibilities, and establishing accountability mechanisms that guide security decision making.
Risk management represents the systematic process of identifying, evaluating, and addressing potential security vulnerabilities. According to research from MITRE, frameworks like the ATT&CK knowledge base provide critical insights into adversary tactics and techniques, enabling organizations to develop more proactive risk mitigation strategies.
Compliance ensures that an organization adheres to relevant legal, regulatory, and industry standards. A comprehensive study examining cybersecurity GRC frameworks highlighted the evolving nature of compliance requirements, particularly with the emergence of new technologies like Large Language Models (LLMs) that introduce complex risk landscapes.
Here is a table that summarizes the three core components of Cybersecurity GRC, their purpose, and example activities related to each as described in this section:
| Component | Purpose | Example Activities |
|---|---|---|
| Governance | Strategic direction & security oversight | Policy development, role definition, accountability |
| Risk Management | Identify, assess & mitigate cyber risks | Vulnerability assessments, threat modeling |
| Compliance | Ensure adherence to regulations & standards | Regulatory alignment, audit trail documentation |
Strategic Implementation of GRC Frameworks
Successful cybersecurity GRC implementation requires a holistic approach that transcends technical controls. Organizations must develop integrated strategies that align security objectives with broader business goals. This involves creating adaptive frameworks capable of responding to dynamic threat environments.
Key implementation strategies include:
- Continuous Monitoring: Establishing real time surveillance of security environments
- Risk Assessment: Regularly evaluating potential vulnerabilities and threat landscapes
- Policy Development: Creating comprehensive yet flexible security guidelines
Federal agencies provide excellent examples of structured GRC implementation. A recent report on federal cybersecurity practices emphasizes the critical role of continuous monitoring and automation in achieving robust risk management frameworks.
Modern cybersecurity GRC frameworks must be agile, capable of adapting to rapidly evolving technological landscapes. This requires ongoing evaluation, periodic reassessment of risk models, and a commitment to integrating emerging security technologies and methodologies.
Organizations that successfully implement comprehensive cybersecurity GRC frameworks position themselves to not just defend against current threats but to anticipate and proactively mitigate potential future security challenges.
Key Benefits and Importance for Businesses
Cybersecurity GRC frameworks have become mission critical for businesses navigating increasingly complex digital environments. These frameworks offer substantial strategic advantages that extend far beyond basic security measures, transforming risk management into a proactive organizational capability.
Financial and Operational Protection
Businesses implementing robust cybersecurity GRC frameworks significantly reduce potential financial losses associated with security breaches. Research on cyber assurance strategies reveals that organizations adopting comprehensive governance frameworks experience substantially lower financial risks and improved operational resilience.
By systematically identifying and mitigating potential vulnerabilities, companies can prevent costly security incidents that might otherwise result in significant economic damage. This includes protecting against financial losses from data breaches, regulatory penalties, legal liabilities, and reputational harm.
Data Protection and Regulatory Compliance
In an era of stringent data protection regulations, cybersecurity GRC frameworks become essential for maintaining compliance. A comprehensive study on data protection governance highlights how these frameworks help organizations align with complex regulatory requirements such as GDPR, HIPAA, and CCPA.
Key compliance benefits include:
- Structured Risk Management: Developing systematic approaches to identifying and addressing data protection risks
- Access Control: Implementing robust mechanisms for managing data access and preventing unauthorized interactions
- Audit Trail Maintenance: Creating comprehensive documentation for regulatory reporting and investigation purposes
Below is a table summarizing the key business benefits of Cybersecurity GRC frameworks as discussed in this section:
| Benefit Area | Specific Advantages/Outcomes |
|---|---|
| Financial Protection | Reduced losses from breaches, lower regulatory fines, minimized liabilities |
| Operational Resilience | Improved incident response, sustained business operations |
| Data Protection & Compliance | Alignment with GDPR, HIPAA, CCPA; strong access controls; audit capability |
| Competitive Advantage | Enhanced trust with customers, partners, stakeholders |
| Strategic Flexibility | Ability to adapt to regulatory and technological changes |
Advanced Technology Integration

Emerging technologies are reshaping cybersecurity GRC approaches. Research on artificial intelligence in governance demonstrates how advanced technologies can enhance risk management processes through machine learning and natural language processing techniques.
Businesses leveraging AI within their GRC frameworks can achieve:
- Predictive Risk Analysis: Using machine learning algorithms to forecast potential security vulnerabilities
- Automated Compliance Monitoring: Implementing real time tracking of regulatory and security requirements
- Enhanced Decision Making: Generating intelligent insights for strategic risk management
Moreover, cybersecurity GRC frameworks provide competitive advantages by demonstrating organizational maturity and commitment to security. They serve as powerful trust signals for customers, partners, and stakeholders, indicating a proactive approach to managing digital risks.
Companies that view cybersecurity GRC not as a compliance burden but as a strategic opportunity will be better positioned to navigate complex technological landscapes, protect their critical assets, and maintain sustained business resilience.
Best Practices for Building an Effective GRC Program
Building an effective Governance, Risk, and Compliance (GRC) program requires a strategic and comprehensive approach that goes beyond mere checklist compliance. Organizations must develop robust frameworks that integrate seamlessly with their overall business objectives and technological infrastructure.
Establishing Strong Governance Foundations
Research from EDUCAUSE emphasizes the critical importance of aligning cybersecurity governance directly with an organization’s mission and strategic goals. This alignment ensures that GRC initiatives are not viewed as isolated technical requirements but as integral components of organizational strategy.
Key governance foundations include:
- Clear Policy Framework: Developing comprehensive and understandable security policies
- Role Definition: Establishing precise responsibilities for cybersecurity management
- Strategic Alignment: Ensuring GRC objectives support broader business objectives
Risk Management and Continuous Assessment
The Center for Internet Security recommends a dynamic approach to risk management that emphasizes continuous monitoring and adaptation. Organizations must move beyond static risk assessments to create flexible, responsive frameworks capable of addressing emerging threats.
Effective risk management strategies involve:
- Regular Risk Assessments: Conducting comprehensive vulnerability evaluations
- Threat Intelligence Integration: Incorporating real time threat data into risk models
- Scenario Planning: Developing robust response strategies for potential security incidents
Implementation and Continuous Improvement
IEEE Computer Society provides critical insights into implementing sustainable GRC programs. The organization highlights the necessity of securing senior management support and creating a culture of continuous learning and improvement.
Key implementation practices include:
- Automated Evidence Collection: Leveraging technology to streamline compliance documentation
- Comprehensive Training: Developing ongoing education programs for employees
- Performance Monitoring: Establishing metrics to track GRC program effectiveness
Successful GRC programs recognize that cybersecurity is not a destination but a continuous journey. Organizations must remain adaptable, investing in technologies and processes that enable rapid response to evolving threat landscapes.
By embracing a holistic, strategic approach to GRC, businesses can transform compliance from a potential burden into a competitive advantage. The most effective programs view cybersecurity not as a technical constraint but as an opportunity to demonstrate organizational resilience and commitment to protecting critical assets.
Cybersecurity GRC Trends and Future Insights
The cybersecurity Governance, Risk, and Compliance (GRC) landscape is rapidly evolving, driven by technological advancements, complex regulatory environments, and increasingly sophisticated cyber threats. Organizations must stay ahead of emerging trends to maintain robust security postures and strategic resilience.
Artificial Intelligence and Automation Transformation
Research on AI in cybersecurity GRC demonstrates the transformative potential of artificial intelligence in enhancing governance processes. Machine learning and natural language processing technologies are revolutionizing how organizations approach risk management and compliance.
Key AI driven GRC innovations include:
- Automated Risk Assessment: Using machine learning algorithms to predict and analyze potential vulnerabilities
- Intelligent Compliance Monitoring: Implementing real time regulatory tracking and interpretation
- Predictive Threat Intelligence: Generating advanced insights into potential security risks
Regulatory Complexity and Global Integration
Insights from cybersecurity experts highlight the increasing complexity of integrating cybersecurity risks within comprehensive governance frameworks. Organizations must develop adaptive strategies that can navigate intricate regulatory landscapes across multiple jurisdictions.
Emerging regulatory trends suggest a need for:
- Comprehensive Global Compliance: Developing flexible frameworks that address international data protection standards
- Cross Border Risk Management: Creating unified approaches to handling diverse regulatory requirements
- Proactive Policy Development: Anticipating and preparing for evolving regulatory landscapes
Data Privacy and Technological Evolution
Professional cybersecurity insights emphasize the critical importance of data privacy considerations in modern GRC strategies. As technological ecosystems become more interconnected, organizations must develop sophisticated approaches to protecting sensitive information.
Future GRC strategies will likely focus on:
- Comprehensive Data Protection: Implementing robust mechanisms for managing complex data privacy requirements
- Advanced Consent Management: Developing granular approaches to user data permissions
- Transparent Governance Models: Creating clear communication channels about data usage and protection
The future of cybersecurity GRC is not about rigid compliance but about creating adaptive, intelligent systems that can anticipate and respond to emerging challenges. Organizations that view GRC as a dynamic, strategic capability rather than a static set of rules will be best positioned to thrive in increasingly complex digital environments.
Successful GRC approaches will require continuous learning, technological innovation, and a holistic understanding of the intricate relationships between technological capabilities, business objectives, and regulatory requirements. The most effective organizations will be those that can seamlessly integrate advanced technologies, human expertise, and strategic thinking into their governance frameworks.
Frequently Asked Questions
What is Cybersecurity GRC?
Cybersecurity Governance, Risk, and Compliance (GRC) refers to a structured approach employed by organizations to manage their cybersecurity posture, aligning security practices with overall business objectives while ensuring compliance with relevant regulations.
Why is GRC important for businesses?
GRC is crucial for businesses as it helps minimize financial losses from data breaches, ensures regulatory compliance, strengthens data protection protocols, and enhances overall operational resilience in the face of cyber threats.
How can organizations implement effective GRC frameworks?
To implement effective GRC frameworks, organizations should establish strong governance foundations, conduct regular risk assessments, develop comprehensive policies, ensure continuous monitoring, and integrate advanced technologies for improved risk management and compliance processes.
What are the emerging trends in Cybersecurity GRC for 2025?
Emerging trends in Cybersecurity GRC for 2025 include the integration of artificial intelligence and automation in governance processes, the increasing complexity of regulatory requirements on a global scale, and a stronger emphasis on data privacy and technological evolution.
Ready to Transform Your Cybersecurity GRC Approach in 2025?
If staying compliant and proactive is slowing your team down, you are not alone. This article highlights just how much security questionnaire overload, scattered risk assessments, and compliance paperwork can block true GRC effectiveness. Imagine if you could streamline these tedious processes and inspire confidence with every security review. The latest GRC trends make it clear: automation and smart integration are essential to gain a real competitive edge.

It is time to turn your GRC pain points into growth opportunities. With Skypher’s AI Questionnaire Automation Tool, your organization can eliminate manual errors and accelerate every security review. Instantly collaborate, automate responses, and connect with leading risk management platforms to stay ahead of constant regulatory changes. Take the first step in modernizing your security compliance and learn how Skypher can help you build trust while driving efficiency. Visit our platform today to start your transformation.





