Companies, regulators, and consumers need to build trust as they address emerging challenges in business, risk management, and compliance. This has attracted the attention of regulators, as many sectors face very high requirements regarding the protection of their information technology (PCI-DSS for Payments or HIPAA for healthcare). Companies are therefore required to frequently go through Vendor Security Assessments (VSAs) as well as making sure their own third parties are secure. Furthermore, these VSAs are getting longer and more complex. If you would like to know more about why security questionnaires are becoming increasingly difficult and demanding, check out our previous blog article.
At Skypher, we have been able to collect data from over 100,000 security questions from our 100+ clients worldwide. Security questionnaires are gathered in 3 formats - Excel documents (71.2%), Online Portals (19.2%) and Word documents (9.6%). The proportion of each format for security questionnaires can be seen in the graph below.

Security questionnaires have not evolved much in their form, as most of them are still done on Word and Excel. To address these repetitive and laborious security questionnaires, we have decided to use Machine Learning and LLM to detect questions in a document and answer them using the company’s knowledge base. At Skypher, we did not forget online portals, that represent 19.2% of security questionnaires and are increasingly used by companies. Our team has therefore focused on our browser extension that works with 40+ online platforms (OneTrust, Prevalent, Archer, ServiceNow, CyberGRX etc.).
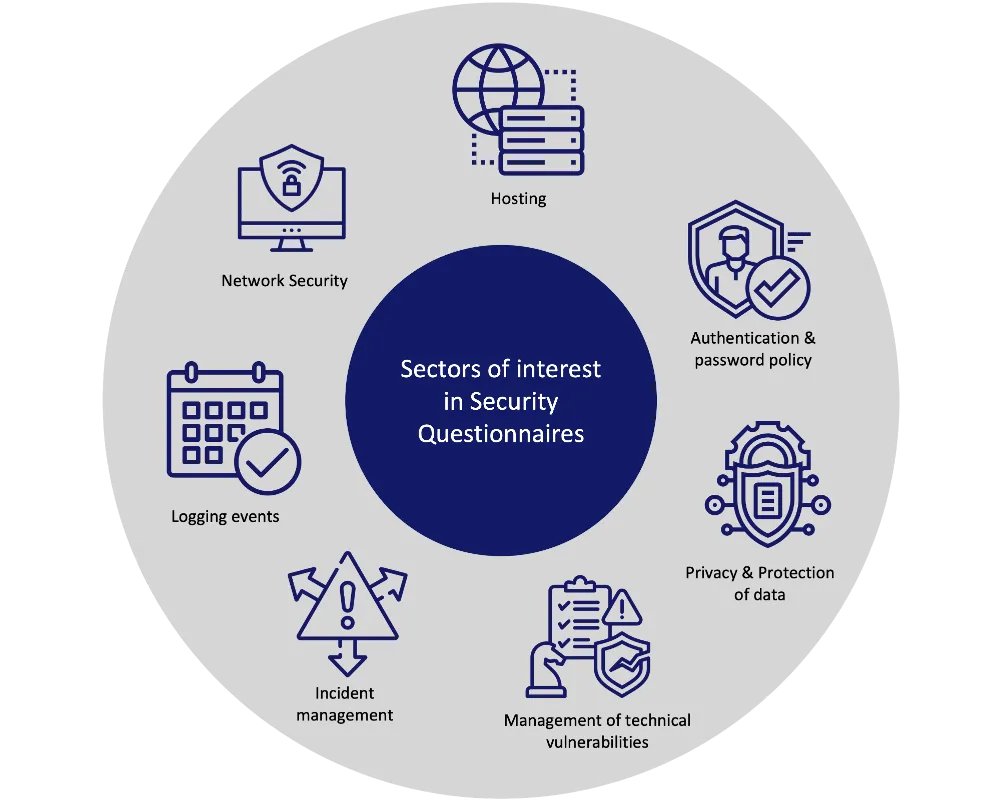
Our database with over 100,000 security questions answered has enabled us to output some analytics regarding the most requested topics by top-tier companies. In the first place, hosting questions account for 14% of overall security questions. Companies' next biggest concerns are authentication & password policies, which account for 13.8%, and privacy & protection of data, which account for 11.5%. A more detailed and exhaustive analysis of the most requested security questions is illustrated in the graph below:

Whenever a company makes a deal, it automatically triggers a security assessment. On top of enabling a security assessment for the organization and its clients, it allows to establish liability in the event of a security breach. Here, we outline some of the most commonly used security frameworks:
While these frameworks provide a structured approach to cybersecurity, they must be customized. Indeed, many organizations rely too much on common standards instead of doing their own risk assessment process regarding their vendors. Organizations should assess their vendors individually depending on the level of access that they have to their internal systems and data.
Our customers often receive security questionnaires that are totally inappropriate to their business or technology. For example, a cloud SaaS solution is usually hosted on the servers of a big cloud provider such as AWS, GCP, or Azure, meaning it should not be audited as a license type of software which manages its own servers and infrastructure. It is also irrelevant to ask questions regarding network or infrastructure to a vendor with a self-hosted solution since you will be managing that, not the vendors. This can lead to a lot of frustration on the vendor side since they have to answer 300 questions that are totally not applicable to their relationship with the organization. Communication and feedback are essential here. Organizations and vendors should maintain open lines of communication, regarding security assessments. Vendors should feel comfortable providing feedback on the appropriateness of the questions that they receive, and organizations should use this feedback to refine their assessment processes over time.
Vendors have significant responsibilities when answering security questionnaires from their customers or partners. It is essential for them to demonstrate their commitment to cybersecurity and to build trust with their clients.
Key responsibilities include:
At Skypher, we provide the software with built-in tools that support the best practices for responding to security questionnaires, used by Fortune 500 companies. With our advanced technology and integrations, you can respond accurately, collaborate seamlessly, along with keeping all records without worrying about the future audit and analysis again.
If you are ready to streamline your process and boost your reliability, book a demo here today and let's discuss how we can help you succeed!
Sources:
https://www.cisecurity.org/controls/v8
https://cloudsecurityalliance.org/
https://www.upguard.com/blog/sig-questionnaire
Ross, R., Pillitteri, V., Dempsey, K., Riddle, M., & Guissanie, G. (2019). Protecting controlled unclassified information in nonfederal systems and organizations (No. NIST Special Publication (SP) 800-171 Rev. 2 (Draft)). National Institute of Standards and Technology.
Discover the latest news from Skypher whether it is features release, new customer stories, guides or updates